What Is a VPN & How Does It Work?
The primary purpose of Virtual Private Network or VPN is to help protect a user's identity and data over public networks including wireless hotspots and the Internet. By creating an encrypted tunnel that is then responsible for transporting data most securely. VPN services are also useful for users to gain access to websites that users in certain countries may only access.
How Does A VPN Work?
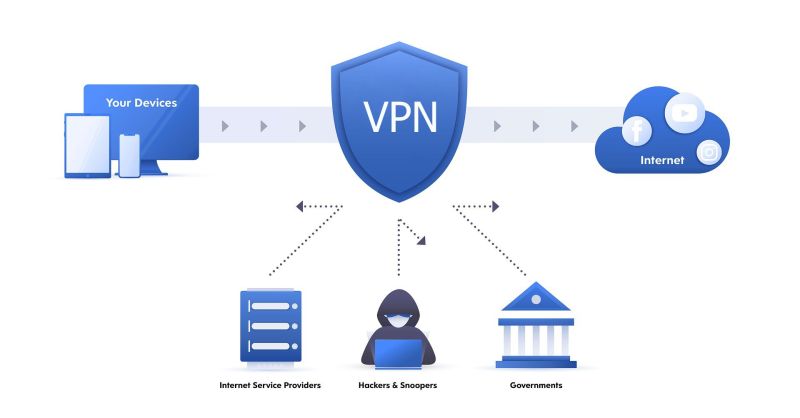
A VPN functions by routing your particular device's online connection through a private server instead of the one provided by your ISP (Internet service provider). That means that as your data gets transmitted online, it comes from that VPN server instead of your computer. The VPN acts as a kind of intermediary when you're connected online. Anytime you connect, you have an IP address, the string of numbers your ISP gives your device. A VPN hides your IP address, which protects your identity. Also, if your data somehow gets intercepted, it will be unreadable before it gets to where it's supposed to be going.
A VPN is like a private tunnel connecting your device and the Internet. It uses encryption to hide your virtual data from prying eyes.
VPN Encryption: The Basics
Encryption is a term for describing how your data stays private whenever you use a VPN. It's the process of encryption that hides your information in a way that makes it look like gibberish unless someone has the key.
The key is a strong encryption key, which breaks the complex code your data is converted into for transmission. The only ones that know the key are the VPN server and your computer or device. Decryption is decoding the data so that applying the key makes the encrypted information again readable and useful.
You might not even know, but this happens anytime you input your credit or debit card details into eCommerce or shopping websites. When you do this, your information should be encrypted, rendering it unreadable until it reaches its final destination.
Various VPN services apply different types of encryption processes. However, most of them follow the same basic pattern.
Anytime you connect to your VPN, it happens through a secure tunnel, where your data gets encoded. This turns your data into an unreadable code as it moves from your device or computer to the VPN server.
Your device will be seen as part of the VPNs local network during this time. That means your IP address is the IP address of one of the VPN servers.
You can browse and use the Internet as you like, with the peace of mind that your VPN is a protective barrier for your personal information. The level of effectiveness and safety your VPN offers you relies on the specific encryption mechanisms and protocols the VPN uses.
VPN server definition
A VPN server enables VPN use. It combines VPN hardware, like physical servers, and VPN software.
Top providers have thousands of servers worldwide. The further the VPN server is from the user's actual location, the worse the performance, so multiple servers are essential. More server locations mean more virtual locations a user can connect to without moving.
Some providers use RAM-only servers. These servers have no external storage, so all data is erased on reboot. VPNs use RAM-only servers to protect user privacy and adhere to no-logs policies.
VPN client definition
A VPN client (or VPN app) connects to a VPN server and encrypts data on your device.
A VPN app (or client) lets you control your VPN connection, tunneling protocol, features, etc. Most VPN providers have apps for Windows, macOS, Android, iOS, Linux, and Amazon Fire TV.
You could also use a VPN without a custom VPN app. Most major operating systems have VPN features. For example, windows networking settings let you set up a VPN connection.
You can also install a VPN client on your wifi router following instructions from a VN provider.
Compare Different Kinds of VPNs
How little or how much your VPN impacts your device is mainly based on the specific type of software you choose. Quite a few VPNs work directly with operating system settings, be it Windows, Android, iOS, or Mac OS. This advantage is that every single app that uses an online connection is protected. This includes Internet browsers, social media, and banking apps.
Standalone VPN Service Providers
Small businesses and homes most frequently use this kind of VPN. These applications create encrypted connections to their respective private networks so you can use them to connect to the broader Internet.
Browser Extensions
A number of VPNs work instead as add-ons to browsers. You can find add-ons to install to Firefox or Chrome, although Opera already has a VPN. These are sometimes easier to use, but the disadvantage is that your data only get protected if you are using that particular browser at the time. Other apps outside the browser don't get protection. Also, browser-based VPNs tend to be more vulnerable, meaning IP leaks are more likely to happen. Always look carefully into browser-based VPN extensions, and stick with reliable names that also do other VPN services. Unfortunately, there are quite a few dirty players in this field. Read the fine print and customer reviews to avoid getting scammed by a data harvester.
Router VPN Services
Using a VPN-enabled router is one more way to utilize a VPN. This is an effective way to go if you have multiple devices you'd like to protect. Instead of doing individual VPN installations, a router VPN will protect every single device that is connected to your router. Also, you only have to sign in once because your router will be forever connected to the VPN you logged into after that.
Connecting a router to your VPN isn't nearly as hard as you might assume. First off, you need a VPN service and a router. It's easiest if you get a router that's already designed for supporting VPNs, so you don't have to do anything technical except put in your VPN details. Unfortunately, such routers typically cost a little more than regular routers, although the sheer convenience is often worth it.
Corporate-Level VPN Services
Businesses, organizations, and other establishments commonly use remote-access VPN services for any staff working outside the office. These VPN services can allow employees to secure access to the company's private intranet, usually just through an app and a password. Unfortunately, this custom-designed solution often involves personalized development and heavy use of IT resources.
VPN Protocols for Different Use Cases
VPN protocols create a secure tunnel between your device and the VPN server. Connecting to a VPN server creates a data tunnel. The connection protocol determines how data is sent over the network.
Some protocols are more secure, some are faster, some work better on mobile devices or older PCs, and some are just outdated.
Internet Key Exchange (IKEv2)
It confirms requests and responses. IKEv2/IPSec is used for authentication. On an unreliable connection, this protocol is very efficient. IKEv2 restores a lost connection. It's one of the fastest tunneling protocols on mobile devices as it can switch between wireless and cellular connections.
OpenVPN
By far the most popular tunneling protocol on desktop apps. This is a free and open-source protocol built on OpenSSL. TCP and UDP are the two types.
- User Datagram Protocol (UDP):
It is much faster because it prevents the recipient from resending data requests. This means less data integrity verification, which allows for more rapid exchanges and, thus, faster speeds. - Transmission Control Protocol (TCP): It allows for multiple data verifications, and the processing time may be longer, limiting your internet speed. Use UDP on trusted networks, while TCP is preferable on public wifi hotspots.
L2TP/IPSec
L2TP isn't encrypted by itself. It confirms requests and answers. IPSec adds encryption to the mix. This protocol was co-developed by the NSA, which raises security concerns. Edward Snowden's revelations suggested the NSA may have L2TP/IPSec backdoors.
WireGuard
Next-generation tunneling protocol. It employs fewer lines of code and maximizes your device's processing power. It is ideal for mobile devices and slower desktops and provides modern encryption and stable connectivity. WireGuard delivers the most extraordinary VPN tunneling performance.
Secure Socket Tunneling Protocol (SSTP)
Microsoft's technology delivers high-level encryption and isn't limited to Windows. Microsoft may have backdoors to access SSTP traffic, notwithstanding its capabilities.
Point to Point Tunneling Protocol (PPTP)
First generally available in the late 1990s. As computational power developed, this protocol's old encryption became vulnerable to brute force attacks. As a result, few VPNs offer this protocol.
Hotspot Shield VPN offers Catapult Hydra.
The company says this protocol improves connection speeds over typical tunneling techniques. However, Hotspot Shield has always been quick, whether owing to Catapult Hydra or other factors.
NordVPN offers NordLynx.
NordLynx solves potential security vulnerabilities while maintaining performance. It is a modified version of the WireGuard protocol.
ExpressVPN offers Lightway.
Based on wolfSSL and an open-source Transport Layer Security (TLS) implementation. It's lightweight for easy maintenance and outstanding performance.
VPN Benefits
When you use a VPN, your device automatically connects to a server. Traffic can be routed through that server. Although this may sound similar to a proxy, there is a distinct difference. Proxies are only capable of redirecting traffic requests. VPNs can route traffic and anonymize it. Better yet, traffic is encrypted when it's sent through a VPN. This prevents cybercriminals from accessing sensitive information.
Read more about the differences between Proxy and VPN
VPNs can encrypt and anonymize all of your traffic on the web. This makes a VPN an excellent choice. VPNs offer many other benefits as well, such as:
Remote access: It's possible to access a VPN network remotely. Because of this, it's becoming increasingly common for businesses to use VPNs. In addition, with a VPN, workers can do more from home.
Secure file sharing: You can do more than visit websites with a VPN. It's also possible to share files. Since VPNs encrypt data, this can be a way to send files securely.
Excellent performance: Surprisingly, a VPN can improve bandwidth and overall efficiency. With a VPN, you may be able to access content faster and accomplish more.
VPN Flaws
VPNs offer numerous advantages, so people are interested in using them for personal and professional purposes. However, VPNs do have some drawbacks that you should be aware of, such as:
VPNs may be blocked: If you're hoping to use a VPN to access content on a streaming site like Netflix, you may not have that option. This is because several content providers block access to VPNs.
Some VPNs employ obsolete, vulnerable protocols. Most leading ISPs have phased out Point-to-Po.int Tunneling Protocol (PPTP)
Real IP address can be leaked. Your true IP address can leak if a VPN server crashes while you're connected. Top VPNs have kill switches that shut your internet when the VPN breaks.
Not all VPNs are equal: If you do choose to use a VPN, it's important to find the right one. VPNs can often deliver a performance boost, but the wrong VPN could slow down your traffic.
Many free VPNs could sell your data. Server maintenance costs money. Free services must get funded somehow. Many VPNs sell your data to third parties.
Some VPNs log user data. Several VPN providers have given government requests for user data. So make sure your VPN doesn't keep logs.
Free versus Paid VPN
These VPN protocols may be obtained for free or for a fee. Unfortunately, free VPN services are not always the best choice. Some risks come with it. For one, there is a possibility of being scammed. Two, the security level offered by free VPN is relatively low. Paid VPN services, on the other hand, offer much higher security levels.
Three, while support is available to paying VPN clients, users cannot expect help from a free service. Fourth, users who want to avoid annoying ads should opt for a paid VPN. As with other free services, public VPNs are swarming with advertisements. This is an inconvenience for users who prefer efficient connection.
The essential criterion in selecting a good VPN provider is integrity. If a user's main aim is to protect his identity and personal data from online threats, he must find a provider capable of providing security, safety, and protection.
Read more: Free versus Paid VPNs compared
FAQ
Are VPNs legal?
The legality of VPNs is a widely debated topic. Most countries have no restrictions on VPNs. Some countries regulate or ban VPNs, but this is uncommon. Using a VPN for unlawful purposes is illegal.
Can a VPN see personal data?
VPN providers can theoretically see your personal data, but many of the top VPNs don't store this information. If a VPN does have this information and it's not that great, it probably isn't the best for you to use.
How much does a VPN cost?
Monthly costs range between $5-12 while annual costs are usually at the lower end of that spectrum, ranging from $3-8 per month. The longer your subscription is, the less you pay per month.
Can a VPN see passwords?
No, VPNs can't read passwords. That's only possible on HTTP websites. Therefore you shouldn't provide your login info there. Most websites use HTTPS to encrypt data and prevent password theft.
Is a VPN the same as wifi?
Even though they work similarly, a VPN is not wifi. Wifi links your device to a server linked to the internet, while a VPN connects you to a server via encrypted tunnels and lets you use its server to access websites and apps.
How does a VPN increase your security?
VPN increases your security by masking your actual IP address from your ISP and encrypting your connection. As a result, VPNs are one of the best cybersecurity and internet privacy solutions.
Can you be tracked with a VPN?
VPN users are hard to track. Cookies, digital fingerprinting, DNS breaches, spyware, and doxxing can trace online behavior even with a VPN. VPNs are great privacy tools, but they don't eliminate tracking risks.
VPN: Worth it?
Yes, a VPN is worth having if you value your privacy and security while browsing, torrenting, or doing anything else online. A VPN can also overcome content restrictions, unblock websites, and prevent ISP speed throttling.